Saturday, February 28, 2009
Agile is the antithesis to security...
Let's face it, there is nothing compelling enterprise IT to get its act together when it comes to security and therefore consumers will still continue to lose data...

Consumers desire that enterprises to write their systems in a secure manner yet most IT professionals have no formal background in computer science, software engineering, etc. Combine this with the fact that most folks in charge of IT aren't truly IT professionals, consumers loosing their data is almost guaranteed.
Most IT professionals are self-taught and learned to program from books (some of which I have written) where companies are further scaling back the amount they spend on training. Others simply don't feel the need to expand their skillsets or thinking beyond banging the next line of code. If I consider my own employer who is gracious enough to provide space for our local OWASP chapter, how many people who work for IBM, Wipro, Cognizant, TCS, Accenture, Satyam and Infosys who are already in the building made the effort to attend? You get the point.
The Dot-Com period gave us the mantra of "make it work, make it work fast, make it scale, make it reliable" as if the last three characteristics can be bolted on after the fact. The Agile movement, while having the best of intentions, has sort of devolved into the overuse of refactoring to cover up the lack of engineering. Corporations have also completely devalued the title of Software Developer by bestowing it upon anyone who can write a shell script or web page.
The title of architect is far too often handed out to a lead developer with the hope that he/she will magically understand all of the technical and non-technical issues involved with application/system/enterprise architecture. So, if you have been promoted to Architect within the last several years, what kind of training did you receive?
While I don't dispute the popularity of the "Quality Triangle", I don't find it particularly useful when doing projects. It's usually used as an excuse for not pushing back on potentially disastrous projects before they start so from my perspective it's a fallacy that supports bad decision making. The real triangle that developers don't seem to have heard of involves three factors:
o Volume of Work to be Performed
o Delivery Schedule
o Resources Available
One cannot avoid the scoping exercise because management or the development team is in a hurry to start coding unless you like cost and schedule overruns. A lot. I still wonder why common sense, that fleeting commodity that should govern decisions, is increasingly uncommon. SCRUM is starting to become a four-letter word in many shops as IT is more about buy-in that developing higher quality software cheaply. When it comes to security, consumers You've been scrummed...

| | View blog reactions
Consumers desire that enterprises to write their systems in a secure manner yet most IT professionals have no formal background in computer science, software engineering, etc. Combine this with the fact that most folks in charge of IT aren't truly IT professionals, consumers loosing their data is almost guaranteed.
Most IT professionals are self-taught and learned to program from books (some of which I have written) where companies are further scaling back the amount they spend on training. Others simply don't feel the need to expand their skillsets or thinking beyond banging the next line of code. If I consider my own employer who is gracious enough to provide space for our local OWASP chapter, how many people who work for IBM, Wipro, Cognizant, TCS, Accenture, Satyam and Infosys who are already in the building made the effort to attend? You get the point.
The Dot-Com period gave us the mantra of "make it work, make it work fast, make it scale, make it reliable" as if the last three characteristics can be bolted on after the fact. The Agile movement, while having the best of intentions, has sort of devolved into the overuse of refactoring to cover up the lack of engineering. Corporations have also completely devalued the title of Software Developer by bestowing it upon anyone who can write a shell script or web page.
The title of architect is far too often handed out to a lead developer with the hope that he/she will magically understand all of the technical and non-technical issues involved with application/system/enterprise architecture. So, if you have been promoted to Architect within the last several years, what kind of training did you receive?
While I don't dispute the popularity of the "Quality Triangle", I don't find it particularly useful when doing projects. It's usually used as an excuse for not pushing back on potentially disastrous projects before they start so from my perspective it's a fallacy that supports bad decision making. The real triangle that developers don't seem to have heard of involves three factors:
o Volume of Work to be Performed
o Delivery Schedule
o Resources Available
One cannot avoid the scoping exercise because management or the development team is in a hurry to start coding unless you like cost and schedule overruns. A lot. I still wonder why common sense, that fleeting commodity that should govern decisions, is increasingly uncommon. SCRUM is starting to become a four-letter word in many shops as IT is more about buy-in that developing higher quality software cheaply. When it comes to security, consumers You've been scrummed...

Friday, February 27, 2009
So, how many non-profit identity organizations exist?
First there was Liberty Alliance, then along came The OpenID Foundation and then Information Card Foundation. I wonder if someone isn't brainstorming an identity foundation for midget women who have mustaches and breakdance while trying to use Cardspace...

From my seat, I see several things wrong with the approach being championed within the identity community. As an employee of a large enterprise, do you think anyone would be successful selling all three? If the goal of identity is to be portable and somewhat unified, why can't their foundations? In the world of non-profits, why do we keep duplicating the same overhead across organizations? How much do to the nature of conversations vary?
So, if I spend say ONE HUNDRED THOUSAND DOLLARS joining these organizations, do I walk away with something other than the ability to influence vendors that I already spend more time that I desire talking to? If I ask the folks over at EMC to incorporate modern approaches to identity into Documentum that they would because I am a member where otherwise they would ignore me?
The world of identity and the world of security need to be connected. Many of the approaches used by the identity community are otherwise insecure. The identity community could provide secure implementations of their offerings if they were to network with another non-profit group known as OWASP. OWASP is more than just a conversation and some documentation. It can provide real lift in code reviewing open source identity implementations.
For the record, I do participate in OWASP not just because of a higher value proposition but because OWASP understands that contributions can be in forms other than writing out large checks. The ability to start of simple by doing things like contributing space for meetings is a great thing and OWASP is very appreciative. Maybe someone can enlighten me as to how to work with the identity crowd in the same fashion...

| | View blog reactions
From my seat, I see several things wrong with the approach being championed within the identity community. As an employee of a large enterprise, do you think anyone would be successful selling all three? If the goal of identity is to be portable and somewhat unified, why can't their foundations? In the world of non-profits, why do we keep duplicating the same overhead across organizations? How much do to the nature of conversations vary?
So, if I spend say ONE HUNDRED THOUSAND DOLLARS joining these organizations, do I walk away with something other than the ability to influence vendors that I already spend more time that I desire talking to? If I ask the folks over at EMC to incorporate modern approaches to identity into Documentum that they would because I am a member where otherwise they would ignore me?
The world of identity and the world of security need to be connected. Many of the approaches used by the identity community are otherwise insecure. The identity community could provide secure implementations of their offerings if they were to network with another non-profit group known as OWASP. OWASP is more than just a conversation and some documentation. It can provide real lift in code reviewing open source identity implementations.
For the record, I do participate in OWASP not just because of a higher value proposition but because OWASP understands that contributions can be in forms other than writing out large checks. The ability to start of simple by doing things like contributing space for meetings is a great thing and OWASP is very appreciative. Maybe someone can enlighten me as to how to work with the identity crowd in the same fashion...

Thursday, February 26, 2009
Virtual Directories and Caching
Mark Wilcox describes some characteristics of caching, but didn't touch on something I think is important...

Microsoft introduced the concept of making their directory services site-aware which translates into the ability for a directory client to bind to the server that is closest to them without having to make developers aware of any particular network topology. This can potentially result in greater availability in that you don't need to procure expensive network load balancers in order for the right decisions to be made.
More importantly, independent of the cost to procure a technology, the more products you use, the more costs go up. For example, in his scenario, the internal employees may be held in Active Directory, customer data in Oracle DB, external customers in OpenDS and he will bring in Oracle Virtual Directory to stitch together information as well as use Oracle Times Ten as a faster way to cache database information. In the short-term, you will most certainly hit your desired performance goal and have been successful in choosing best of breed. Now, fast forward five years from now and ask yourself when IT costs more than it should, how could this have been done cheaper!
If some of your data is already in an LDAP format, what would have prevented you from putting relational data in an LDAP store and then replicating? So is caching all about another product, another tier or can you accomplish the goal via things you already have such as the ability to replicate using the functionality of products you already have...

| | View blog reactions
Microsoft introduced the concept of making their directory services site-aware which translates into the ability for a directory client to bind to the server that is closest to them without having to make developers aware of any particular network topology. This can potentially result in greater availability in that you don't need to procure expensive network load balancers in order for the right decisions to be made.
More importantly, independent of the cost to procure a technology, the more products you use, the more costs go up. For example, in his scenario, the internal employees may be held in Active Directory, customer data in Oracle DB, external customers in OpenDS and he will bring in Oracle Virtual Directory to stitch together information as well as use Oracle Times Ten as a faster way to cache database information. In the short-term, you will most certainly hit your desired performance goal and have been successful in choosing best of breed. Now, fast forward five years from now and ask yourself when IT costs more than it should, how could this have been done cheaper!
If some of your data is already in an LDAP format, what would have prevented you from putting relational data in an LDAP store and then replicating? So is caching all about another product, another tier or can you accomplish the goal via things you already have such as the ability to replicate using the functionality of products you already have...

Wednesday, February 25, 2009
The Amphibian of Identity Protocols
Anyone ever noticed how Mark Wilcox of Oracle, Pat Patterson of Sun and Kim Cameron of Microsoft all do a wonderful job of interacting with their customers in the blogosphere. Maybe someone could tell me why EMC is so horrific in this regard...

Anyway, back to something Mark said that I disagree with. His comment was:
Nowadays, business users understand UML notation as they may have been participants in RUP. Likewise, having a common notation in which to convey ideas is equally important in the new world where developers may be in India and need to communicate with the person who controls the schema who could be employed by another firm.
Indpendent of the tree structure which should be kept simple, one still should model objectClasses. In a large enterprise, you may desire to have different types of people that are extended from say Person or its derivatives. Independent of any inheritance construct, you may also want to indicate to developers via a model that say oraclePerson should be stored in ou=people where dfsPerson should be stored in ou=fugly. Anyway, I hope you will reach out to your customers and explore this thought deeper. Ludovic Poitou of Sun will hopefully share his thoughts in this regard as well.
As far as commentary regarding LDAP injection, I believe that it would be great if Mark and others from the LDAP crowd could spend more time understanding OWASP and not only at a personal level, but how their employer could benefit by becoming a member. In his example, he assumes that SQL injection type attacks require update capability where it may be sufficient to do things that are based on being read-only. So if I could read your credit card, SSN or whatever goodies you have in a directory then I don't think that write protection matters. Likewise, using OVD as a type of firewall is somewhat intriguing but also flawed. Maybe he could outline exactly what the constraint would look like since the odds are that the application would have valid rights to read the data just not in the exploited context.
In order to get to a higher-level of security, we would have to acknowledge that ACLs are suboptimal, that CARML-style declarations are nice but aren't industrial-strength enforcement mechanisms in an OWASP-style threat model...

| | View blog reactions
Anyway, back to something Mark said that I disagree with. His comment was:
- I don't think there is a need to model LDAP anymore - because applications basically dictate the organization and it's generally better to keep it simple. Have a root (e.g. dc=oracle,dc=com) and then have a couple of branches (e.g. ou=people, cn=users).
Nowadays, business users understand UML notation as they may have been participants in RUP. Likewise, having a common notation in which to convey ideas is equally important in the new world where developers may be in India and need to communicate with the person who controls the schema who could be employed by another firm.
Indpendent of the tree structure which should be kept simple, one still should model objectClasses. In a large enterprise, you may desire to have different types of people that are extended from say Person or its derivatives. Independent of any inheritance construct, you may also want to indicate to developers via a model that say oraclePerson should be stored in ou=people where dfsPerson should be stored in ou=fugly. Anyway, I hope you will reach out to your customers and explore this thought deeper. Ludovic Poitou of Sun will hopefully share his thoughts in this regard as well.
As far as commentary regarding LDAP injection, I believe that it would be great if Mark and others from the LDAP crowd could spend more time understanding OWASP and not only at a personal level, but how their employer could benefit by becoming a member. In his example, he assumes that SQL injection type attacks require update capability where it may be sufficient to do things that are based on being read-only. So if I could read your credit card, SSN or whatever goodies you have in a directory then I don't think that write protection matters. Likewise, using OVD as a type of firewall is somewhat intriguing but also flawed. Maybe he could outline exactly what the constraint would look like since the odds are that the application would have valid rights to read the data just not in the exploited context.
In order to get to a higher-level of security, we would have to acknowledge that ACLs are suboptimal, that CARML-style declarations are nice but aren't industrial-strength enforcement mechanisms in an OWASP-style threat model...

Tuesday, February 24, 2009
How come the marketplace no longer loves Sun Microsystems
In conversations with CIOs and enterprise architects in other Fortune enterprises, no one considers Sun a strategic vendor! I wonder what they are doing wrong?

I know it has absolutely nothing to do with the quality of their engineering staff as folks such as Pat Patterson, Ramesh Nagappan, Roman Ivanov, James Gosling, Yasuhiro Fujitsuki and others are smart, helpful and have lots of interaction with their communities.
This leads me to believe that Sun isn't being out-engineered but is being outsold in a few areas. First, I can say within a work context that I have lots of interaction with the Microsoft and Oracle sales folks whom aren't just doing thinly veiled sales pitches but actually help make me smarter at a technical level by sending me information that they personally know I am interested in. They both have worked to introduce me to their customers in other shops that use the same technology and have been great supporters of things I care about outside of work such as sponsoring our local OWASP chapter meetings. I have no freakin clue as to who the sales folks from Sun are on my side of town let alone any of the other higher value stuff.
For enterprise architects that love to be spoonfed by Gartner, Sun hasn't been working the magic (or submitting to extortion) by appearing in lots of Gartner magic quadrants. Maybe they have underestimated the value of paying excessive fees for analyst services and think that just because they believe it is a waste of money that everyone else may hold a similar opinion.
If I were to compare Nishant Kaushik and Mark Wilcox of Oracle to Pat Patterson and Ludovic Poitou of Sun who have analogous roles, which body do you think was last to speak to analysts at the 451 Group, Nemertes, Burton and Redmonk?
One of the more interesting observations I have noted in many vendor presentations is how vendors buy stuff from each other which causes the customer list to appear large. For example, if Ounce labs shows in their sales deck how Oracle is a customer, it is almost always true that they are probably using Oracle CRM and this team would show Ounce Labs on their deck. For Sun, it seems as if they are too indoctrinated into the we are smarter than everyone else and reinvent everything inhouse syndrome. I bet the world has no freakin clue as to what technologies Sun uses in its own ecosystem that it didn't invent.
Did you know that the local Microsoft office holds user groups on various technologies and you don't need to register nor be an MS customer to attend? Microsoft technical events at the local level aren't turned into sales leads and are great forums for folks to interact without any followon pressure.
My local OWASP chapter meetings follow the same process where I discourage the notion of RSVP. I simply refuse to track people as I believe this is a characteristic of being open. If you are going to be open, you have to be so in all aspects...

| | View blog reactions
I know it has absolutely nothing to do with the quality of their engineering staff as folks such as Pat Patterson, Ramesh Nagappan, Roman Ivanov, James Gosling, Yasuhiro Fujitsuki and others are smart, helpful and have lots of interaction with their communities.
This leads me to believe that Sun isn't being out-engineered but is being outsold in a few areas. First, I can say within a work context that I have lots of interaction with the Microsoft and Oracle sales folks whom aren't just doing thinly veiled sales pitches but actually help make me smarter at a technical level by sending me information that they personally know I am interested in. They both have worked to introduce me to their customers in other shops that use the same technology and have been great supporters of things I care about outside of work such as sponsoring our local OWASP chapter meetings. I have no freakin clue as to who the sales folks from Sun are on my side of town let alone any of the other higher value stuff.
For enterprise architects that love to be spoonfed by Gartner, Sun hasn't been working the magic (or submitting to extortion) by appearing in lots of Gartner magic quadrants. Maybe they have underestimated the value of paying excessive fees for analyst services and think that just because they believe it is a waste of money that everyone else may hold a similar opinion.
If I were to compare Nishant Kaushik and Mark Wilcox of Oracle to Pat Patterson and Ludovic Poitou of Sun who have analogous roles, which body do you think was last to speak to analysts at the 451 Group, Nemertes, Burton and Redmonk?
One of the more interesting observations I have noted in many vendor presentations is how vendors buy stuff from each other which causes the customer list to appear large. For example, if Ounce labs shows in their sales deck how Oracle is a customer, it is almost always true that they are probably using Oracle CRM and this team would show Ounce Labs on their deck. For Sun, it seems as if they are too indoctrinated into the we are smarter than everyone else and reinvent everything inhouse syndrome. I bet the world has no freakin clue as to what technologies Sun uses in its own ecosystem that it didn't invent.
Did you know that the local Microsoft office holds user groups on various technologies and you don't need to register nor be an MS customer to attend? Microsoft technical events at the local level aren't turned into sales leads and are great forums for folks to interact without any followon pressure.
My local OWASP chapter meetings follow the same process where I discourage the notion of RSVP. I simply refuse to track people as I believe this is a characteristic of being open. If you are going to be open, you have to be so in all aspects...

Monday, February 23, 2009
Sun vs Oracle
One of my 2009 New Years Resolutions is to encourage both Sun Microsystems and Oracle to become paid members of OWASP. Anyone care to speculate which one will be first?

| | View blog reactions
Sunday, February 22, 2009
I have been invited to join another advisory board and am annoyed...
I am flattered when some vendor invites me to serve on their advisory board when it is under the guise of helping them make a better product. Likewise, I am disgusted when they attempt to use the notion of an advisory board role as a sales tactic...

I have a genuine interest in helping others build hiqh-quality valuable working software that benefits humanity. I don't have an interest in either being baited via this channel and leveraged to penetrate my own employer nor to be leveraged as a cheap lead generation mechanism so that you can annoy my industry peers.
Going forward, any vendor that attempts to use this tactic will be called out publicly in my blog...

| | View blog reactions
I have a genuine interest in helping others build hiqh-quality valuable working software that benefits humanity. I don't have an interest in either being baited via this channel and leveraged to penetrate my own employer nor to be leveraged as a cheap lead generation mechanism so that you can annoy my industry peers.
Going forward, any vendor that attempts to use this tactic will be called out publicly in my blog...

Saturday, February 21, 2009
More Thoughts on CMIS
I have learned a lot regarding CMIS from Pie and had some additional thoughts on how this specification can be improved...


| | View blog reactions
- I’m torn here. I believe that CMIS should be 100% supported, but it does not cover everything. There will always be some vendor specific features that will need to be listed.
- As for XACML, it is out and it doesn’t appear to have been close. I’m guessing it has to do with simplicity.
- I feel that taking DFS out of the loop would make for a more efficient implementation.
- This needs to be easy. There are pros and cons to every choice here. Clear documentation is what will help, regardless of the choice. I prefer more self-describing, but I would rather other’s chimed-in on this one.
- How should compression be handled within an ECM SOA? Carefully? This is actually a concern of mine. Simple use-case, a scanned image sits in a repository. It has been decreed that at the stored resolution, it meets the requirements to be a record. Now you compress it for transmission to the consumer application. Is it still an official copy, or just a referential copy for research purposes? I don’t know the answer to that question.

Friday, February 20, 2009
Do software vendors lie when responding to RFPs...
CIO Magazine outlines the challenges of getting software vendors and IT consultancies to not fib when responding to RFPs, I figured I would provide a few tips...

If you work for a insultancy and are on the bench, regardless of your knowledge of a particular technology or approach, you are usually assigned the duty to respond to RFPs. After all, they are paying your salary and therefore want you to be productive. So, clients expect an RFP will be answered by those in the know or at least reviewed but perception is far from reality.
So, how come clients aren't asking for the BIOs of those who are actually creating the meat of the response and comparing it with the proposed team members and the bios within? I bet they would learn a lot as to the randomness of responses received. When I was a consultant in the early days of my career, I also found another problem in that I was beat down pretty early in the game by boilerplate senseless questions that are asked solely for process reasons. When do you think the last time I saw an RFP that was going to be sent to Microsoft where one of the questions was do they support the Windows platform. When receiving idiotic, boneheaded, braindead questions, my creative juices start to flow and I dream up fluid bullshit vs thinking about an answer than would have been insightful and informative.
I vividly remember my sixth grade English teacher whom taught us how to turn every question into an answer. This politician tactician tactic works like a charm as when folks hear their own voice echoed, it seems to bring a smile to them which reminds me of blowing smoke up something. Seriously, wouldn't you get better answers if your questions were more boolean? For example, Hey Microsoft! can you run Windows 2008 Server on an IBM PC/JR vs Microsoft, please outline all the devices that your operating system can run on?
So, what ever happened to actually proving out working software? I know it is so freakin difficult to prove out anything in modern corporate environments as your infrastructure team is most certainly guaranteed to be an impediment. Let's acknowledge that to complete something as simple as installing Hello World in a modern process-oriented enterprise can easily take six months, doesn't mean that you outsource responsible decision-making and can use documentation as a substitute for working software...

| | View blog reactions
If you work for a insultancy and are on the bench, regardless of your knowledge of a particular technology or approach, you are usually assigned the duty to respond to RFPs. After all, they are paying your salary and therefore want you to be productive. So, clients expect an RFP will be answered by those in the know or at least reviewed but perception is far from reality.
So, how come clients aren't asking for the BIOs of those who are actually creating the meat of the response and comparing it with the proposed team members and the bios within? I bet they would learn a lot as to the randomness of responses received. When I was a consultant in the early days of my career, I also found another problem in that I was beat down pretty early in the game by boilerplate senseless questions that are asked solely for process reasons. When do you think the last time I saw an RFP that was going to be sent to Microsoft where one of the questions was do they support the Windows platform. When receiving idiotic, boneheaded, braindead questions, my creative juices start to flow and I dream up fluid bullshit vs thinking about an answer than would have been insightful and informative.
I vividly remember my sixth grade English teacher whom taught us how to turn every question into an answer. This politician tactician tactic works like a charm as when folks hear their own voice echoed, it seems to bring a smile to them which reminds me of blowing smoke up something. Seriously, wouldn't you get better answers if your questions were more boolean? For example, Hey Microsoft! can you run Windows 2008 Server on an IBM PC/JR vs Microsoft, please outline all the devices that your operating system can run on?
So, what ever happened to actually proving out working software? I know it is so freakin difficult to prove out anything in modern corporate environments as your infrastructure team is most certainly guaranteed to be an impediment. Let's acknowledge that to complete something as simple as installing Hello World in a modern process-oriented enterprise can easily take six months, doesn't mean that you outsource responsible decision-making and can use documentation as a substitute for working software...

Thursday, February 19, 2009
Enterprise Architecture: How much should I get paid?
It is the time of annual reviews in many corporations and therefore I will share some thoughts on worst practices in compensating IT professionals...

Traditional pay structures work on the false assumption that people behave rationally. A wise architect I know once said that enterprises are nothing but coffee klatch where silly little human beings can feel good about themselves regardless of business outcome. So, the notion of every employee pulling together to generate profits is the first worst practice. Many compensation plans assume this to be true and therefore rationalize that one should get paid more for higher profits and therefore pay becomes a motivating factor.
Let's agree that the problem of compensation is asymmetric in that you can pay someone for making profits, but you can't penalise them for making losses. Virtually no employee will work for a company if there are circumstances in which they would have to pay for the privilege. This translates into some doing the bare minimum in order to still maintain the floor of compensation.
Has anyone noticed that in a perception management culture there are now more folks who instead of playing to win; play to not lose! We all throw daggers at Wall Street executives for their short-term thinking but haven't realize that we also exhibit the same thought patterns. Even if we weren't to look in the mirror, we at least need to acknowledge that it isn't always obvious in the short term what benefits the company the most.
Many of us love to abuse the word risk which is distinct from the real word we should use to describe our behavior, which is loss. Money is used as a scorecard to determine where one ranks against an arbitrarily decided peer group. Anecdotally it seems likely that people work hard to increase their bonus not mainly because of the associated material benefits but because it governs their place in the hierarchy of their social group.
Do you want a big bonus just because you worked hard and earned it, or do you want a big bonus because you believe in your own mind that you deserve more compensation that your peer regardless of circumstance? Anyway, if enterprises are going to be successful in a declining economy, we need to modernize management theory and noodle ways to motivate people in a non-financial way.
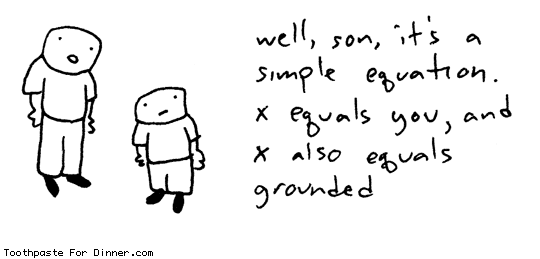
| | View blog reactions
Traditional pay structures work on the false assumption that people behave rationally. A wise architect I know once said that enterprises are nothing but coffee klatch where silly little human beings can feel good about themselves regardless of business outcome. So, the notion of every employee pulling together to generate profits is the first worst practice. Many compensation plans assume this to be true and therefore rationalize that one should get paid more for higher profits and therefore pay becomes a motivating factor.
Let's agree that the problem of compensation is asymmetric in that you can pay someone for making profits, but you can't penalise them for making losses. Virtually no employee will work for a company if there are circumstances in which they would have to pay for the privilege. This translates into some doing the bare minimum in order to still maintain the floor of compensation.
Has anyone noticed that in a perception management culture there are now more folks who instead of playing to win; play to not lose! We all throw daggers at Wall Street executives for their short-term thinking but haven't realize that we also exhibit the same thought patterns. Even if we weren't to look in the mirror, we at least need to acknowledge that it isn't always obvious in the short term what benefits the company the most.
Many of us love to abuse the word risk which is distinct from the real word we should use to describe our behavior, which is loss. Money is used as a scorecard to determine where one ranks against an arbitrarily decided peer group. Anecdotally it seems likely that people work hard to increase their bonus not mainly because of the associated material benefits but because it governs their place in the hierarchy of their social group.
Do you want a big bonus just because you worked hard and earned it, or do you want a big bonus because you believe in your own mind that you deserve more compensation that your peer regardless of circumstance? Anyway, if enterprises are going to be successful in a declining economy, we need to modernize management theory and noodle ways to motivate people in a non-financial way.
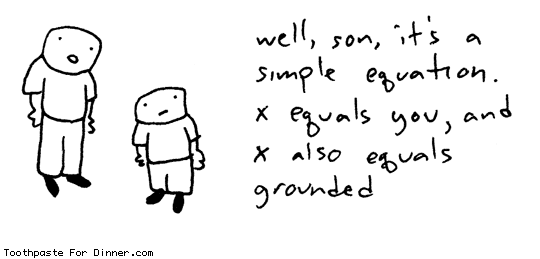
Wednesday, February 18, 2009
Enterprise Architecture: So, exactly what is a best practice?
There are way too many enterprise architect's who behave like ass clowns by taking the notion of best practices as holy doctrine...

There’s nothing funnier than someone who has been practicing a particular technology for six months spouting off about them. Well actually there is, and that’s the vendor spouting off about them, especially when the so called best practice is supporting their latest attempt to cover up a weakness in the product. Ever notice which bloggers always talk about best practices? I wonder what they are attempting to hide?
Let's agree that best practices are only best practices when you understand the context in which they are created and are not meant to be religion. Below are a few considerations when noodling them:

| | View blog reactions
There’s nothing funnier than someone who has been practicing a particular technology for six months spouting off about them. Well actually there is, and that’s the vendor spouting off about them, especially when the so called best practice is supporting their latest attempt to cover up a weakness in the product. Ever notice which bloggers always talk about best practices? I wonder what they are attempting to hide?
Let's agree that best practices are only best practices when you understand the context in which they are created and are not meant to be religion. Below are a few considerations when noodling them:
- Usually does not account for industry verticals or company culture: Gartner boilerplate templates that are stamped out in an arbitrary fashion need to be customized within a vertical context in order to be truly useful. Organizations are unique in that each has its own characteristics of what works and what doesn't. Presupposed analyst genralizations are a trap.
- Most don't account for the underlying process: Best practices normally demonstrate a procedure that results in a more efficient approach to get the best results. As a result there is often very little attention that is paid to the underlying considerations that are below the surface. This results in a considerable maintenance obstacle since an organization might not then have the expertise to measure and interpret variability. This is probably one of the biggest reasons why India outsourcing sucks.
- Flexibility is paramount: However some when delivered come off so rigid that it is the exact opposite, people try to tailor business to platform, not platform to business. The round peg / square hole metaphor is alive in most shops that observe best practices.
- Best practices typically lack objective measure: One mans best practice, is another mans worst design! When you are a hammer, everything looks like a nail. This reminds me of PMI indoctrination and CMMi process-orientation.
- There are no easy answers to difficult questions: Has anyone ever asked a question that sounds like: I am attempting to customize the portal navigation to include external resources and security is getting in the way?what might seem a simple thing is nothing of the sort and simply cannot be answered without in depth analysis, and besides there is no best practice here. There are no easy answers to difficult questions, unless you count the default answer of a security "consultant”, which is of course, “no”.
Tuesday, February 17, 2009
How come Redmonk is the only analyst firm that cares about transparency?
Ever notice how transparent the folks from Redmonk are? What can Gartner learn from them?

Their clients are posted clearly on their site. Every time they mention a client (in a blog or otherwise) they include the disclaimer. I see them as being more of a pulse on what's going on than a mouthpiece for clients (e.g. Gartner). I never feel like I have to look at their research with a microscope and wonder if any string manipulation is going on. I know that many are curious how many companies have ever been in the Gartner Magic Quadrant without paying fees but if Redmonk had their own, this too would be transparent.
What I find even more fascinating is the readership of Redmonk which is equally transparent. If you want to know who is reading Redmonk, then all you have to do is go to Google to check links or simply look at web page statistics by third parties. Can you ask the same question with the same amount of visibility for content produced by Gartner.
While I am not employed by any software vendor, it feels like many of them are throwing away their money by not getting exactly what they think. Gartner is the model for what's wrong with the industry analyst community and I am curious when others will see the wisdom of the Redmonk model...
NOTE: James McGovern is not a Redmonk client...

| | View blog reactions
Their clients are posted clearly on their site. Every time they mention a client (in a blog or otherwise) they include the disclaimer. I see them as being more of a pulse on what's going on than a mouthpiece for clients (e.g. Gartner). I never feel like I have to look at their research with a microscope and wonder if any string manipulation is going on. I know that many are curious how many companies have ever been in the Gartner Magic Quadrant without paying fees but if Redmonk had their own, this too would be transparent.
What I find even more fascinating is the readership of Redmonk which is equally transparent. If you want to know who is reading Redmonk, then all you have to do is go to Google to check links or simply look at web page statistics by third parties. Can you ask the same question with the same amount of visibility for content produced by Gartner.
While I am not employed by any software vendor, it feels like many of them are throwing away their money by not getting exactly what they think. Gartner is the model for what's wrong with the industry analyst community and I am curious when others will see the wisdom of the Redmonk model...
NOTE: James McGovern is not a Redmonk client...

Links for 2009-02-17
I wonder if this posting ever answered the original question asked by Mark Wilcox?
A nice look at how KFC leverages SAML
It is interesting to see that Facebook will support OpenID but hopefully they will allow others to be the identity provider and will defer trust to others.
While email encryption is the most discussed use-case, the blogosphere needs to take this a lot deeper in terms of its analysis. Luther Martin responded back with some insight that technically is an answer but still is otherwise weak. He accurately describes that there are not one but two schemes underlying IBE but gets it twisted by focusing on whether customers understand the distinctions between them when the focus from a customer perspective is in choosing solutions with only two. Traditional PKI in this regard doesn't have just two pluggable asymmetric algorithms but at least dozens. Having more choice in of itself is more secure independent of any crypto review of any particular algorithm.
In another post, he asks the question of Is interoperable key management dead? I believe the question should be how many key management solutions should an enterprise have? As a customer, should I have Voltage for email, IBM for tape encryption, RSA for document storage, and so on. Independent of any standards, vendors need to talk more transparently about how their solutions may never be eliminated and/or rationalized. Of course there were other aspects of the original posting that I am sure Luther and his friends could provide insight on

Monday, February 16, 2009
Team OWASP on Kiva
Kiva is a non-profit website that allows you to lend as little as $25 to a specific low-income entrepreneur in the developing world. You choose who to lend to - whether a baker in Afghanistan, a goat herder in Uganda, a farmer in Peru, a restaurateur in Cambodia, or a tailor in Iraq - and as they repay the loan, you get your money back.
Check out the OWASP lending team, and learn more about lending teams on Kiva in general, by clicking here.
I haven't had anyone yet join from Infosys, Wipro or Accenture...

| | View blog reactionsCheck out the OWASP lending team, and learn more about lending teams on Kiva in general, by clicking here.
I haven't had anyone yet join from Infosys, Wipro or Accenture...

When is it OK to appear clueless in front of business customers?
Has anyone else noticed the trend lately that vendors appear less polished when presenting to their clients...

I remember the days of being a consultant, where we would prepare our pitch, the dog and pony show. We would anticipate questions that customers would ask and figure out the answers beforehand. We would also ensure that whenever interacting with clients, we would have a real subject matter expert on hand. Today, this practice seems to be disappearing.
Nowadays, clients are bombarded with sales engineers (oxymoron) whom only know the canned speech and present thinly-veiled, media relations sanitized presentations that lack substance. Whenever a client either out of ignorance or just inquisitiveness manages to take the discussion offtrack, their entire presentation derails.
Indian outsourcing firms don't have enough depth to be smarter than most clients and therefore leverage process as a way to get the client to spoonfeed them information. Software vendors blow up my phone on an almost daily basis with a hook and arrow line that starts with some generic mindless Gartner like statement, proceeded by tongue-twisting name dropping of other recognizable Fortune enterprises and concludes with asking for what challenges I have that their solution could solve for. Don't this seem flawed?
I remember talking to one salesperson and asking a basic question like what do you think our company does? He didn't even know that we sell insurance, investments, etc. Feeling kinda stupid, he proceeded to bring himself back to his script and started to talk about open source. I asked him a question of whether anyone in his company blogs. The silence was deafening. He then proceeded to try again, under the guise of three strikes and your out by mentioning what Gartner had to say about them. Of course, I asked if Forrester, Burton Group, The 451 Group, RedMonk, Nemertes, Entiva and other analyst firms I respect had any opinion. He confided in me and said that he never heard of these firms and commented that he would do some homework on them though. I mentioned that he should ask when having a conversation with potential clients, he should ask which analyst firms they pay attention to the most...

Could you imagine having to tell your mechanic how to do an oil change? Of course not, this would feel silly, yet I bet many clients of infrastructure providers and indian outsourcing firms do this exact thing on a repeatable basis. From the perspective of these firms, if clients are idiotic enough to pay someone to not have a clue then they deserve to be exploited. After all, if I could keep hundreds, if not thousands of folks whom otherwise add zero value in a revenue generation scenario, this is good for business, good for profits and good for the economy.
I find it equally fascinating that the partners in various consulting firms no longer care as they are focused on short-term results. Of course, this comes at the expense of long-term relationships. In business 101, I learned that if you can develop a customer-relationship based on competency, integrity and expediency then selling gets a whole lot easier which begs the question of why are companies making their jobs harder.
So, if I were to ping folks over at MomentumSI for SOA, Cigital for security or Washington Consulting for ECM, should I expect that they solely have knowledgable folks or should clients also expect them to have tools in their toolbox? More importantly, should clients check to see that the tools exist before engaging?
At some level, someone in the blogosphere would be awarded hero status if they crafted a list of ten things to know before presenting a sales pitch to an enterprise customer prospect. In the meantime, if you are an employee of a vendor, please consider updating your 2009 resolutions to include not looking clueless in front of enterprise customers. It would be greatly appreciated...

| | View blog reactions
I remember the days of being a consultant, where we would prepare our pitch, the dog and pony show. We would anticipate questions that customers would ask and figure out the answers beforehand. We would also ensure that whenever interacting with clients, we would have a real subject matter expert on hand. Today, this practice seems to be disappearing.
Nowadays, clients are bombarded with sales engineers (oxymoron) whom only know the canned speech and present thinly-veiled, media relations sanitized presentations that lack substance. Whenever a client either out of ignorance or just inquisitiveness manages to take the discussion offtrack, their entire presentation derails.
Indian outsourcing firms don't have enough depth to be smarter than most clients and therefore leverage process as a way to get the client to spoonfeed them information. Software vendors blow up my phone on an almost daily basis with a hook and arrow line that starts with some generic mindless Gartner like statement, proceeded by tongue-twisting name dropping of other recognizable Fortune enterprises and concludes with asking for what challenges I have that their solution could solve for. Don't this seem flawed?
I remember talking to one salesperson and asking a basic question like what do you think our company does? He didn't even know that we sell insurance, investments, etc. Feeling kinda stupid, he proceeded to bring himself back to his script and started to talk about open source. I asked him a question of whether anyone in his company blogs. The silence was deafening. He then proceeded to try again, under the guise of three strikes and your out by mentioning what Gartner had to say about them. Of course, I asked if Forrester, Burton Group, The 451 Group, RedMonk, Nemertes, Entiva and other analyst firms I respect had any opinion. He confided in me and said that he never heard of these firms and commented that he would do some homework on them though. I mentioned that he should ask when having a conversation with potential clients, he should ask which analyst firms they pay attention to the most...

Could you imagine having to tell your mechanic how to do an oil change? Of course not, this would feel silly, yet I bet many clients of infrastructure providers and indian outsourcing firms do this exact thing on a repeatable basis. From the perspective of these firms, if clients are idiotic enough to pay someone to not have a clue then they deserve to be exploited. After all, if I could keep hundreds, if not thousands of folks whom otherwise add zero value in a revenue generation scenario, this is good for business, good for profits and good for the economy.
I find it equally fascinating that the partners in various consulting firms no longer care as they are focused on short-term results. Of course, this comes at the expense of long-term relationships. In business 101, I learned that if you can develop a customer-relationship based on competency, integrity and expediency then selling gets a whole lot easier which begs the question of why are companies making their jobs harder.
So, if I were to ping folks over at MomentumSI for SOA, Cigital for security or Washington Consulting for ECM, should I expect that they solely have knowledgable folks or should clients also expect them to have tools in their toolbox? More importantly, should clients check to see that the tools exist before engaging?
At some level, someone in the blogosphere would be awarded hero status if they crafted a list of ten things to know before presenting a sales pitch to an enterprise customer prospect. In the meantime, if you are an employee of a vendor, please consider updating your 2009 resolutions to include not looking clueless in front of enterprise customers. It would be greatly appreciated...

Sunday, February 15, 2009
Random Thoughts for 2009-02-15

Saturday, February 14, 2009
Gartner releases paper on Static Analysis
Figured I would share thoughts on the quality of Gartner research in the static analysis space...

Gartner analyst's Joseph Feiman and Neil MacDonald have created the Magic Quadrant for Static Application Security Testing for the fine price of $1,995. Of course they focused on productecture and provided interesting insights into particular vendors such as Ounce Labs, Fortify Software, Coverity, etc but not in a way that is actionable.
For example, they mentioned that Fortify software has a heavy sales model that has annoyed customers but didn't say why this existed. Is it because of the way that products are licensed where folks need to have ongoing interaction with sales folks over the long haul or is it because they have too many sales people that don't have nothing better to do or is it because at some level enterprisey types like the attention and being annoyed is actually a good thing.
Some of my enterprise architect peers love the vendor sales guys. After all, they have an expense account and can take you to fancy restaurants. There is a secret relationship between sales people and enterprise architects that is rarely discussed in public. Some sales guys will allow the enterprise architect to outsource the sales pitch, the dog and pony show the enterprise architect themselves should be doing. So, if you work for one of those shops where you are an enterprise architect but otherwise are clueless, then the commentary of Gartner may not be a negative.
Is security based on superficial things you can count such as number of languages or could it be based on the ability for information to be distilled to non-developer demographics. It is important to acknowledge that static analysis is very useful for helping developers write more secure code but it has a side effect in that it can be used for management purposes as well. Consider a scenario where I may have two Indian outsourcing firms where your otherwise non-technical CIO may want to know whether Cognizant writes more secure code than say Infosys or Wipro. The reporting capabilities may be more important in some shops than its actual ability to help developers.
I find it fascinating that Gartner was notoriously silent on mentioning ways to evaluate static analysis tools. Most folks know that the OWASP WebGoat project serves as a test harness for many of these tools. I have always wondered whether it has anything to do with the fact that other analyst firms have beat Gartner in terms of participation in OWASP? For example, Chenxi Wang of Forrester has participated in user groups and conferences and the same thing can be said of the 451 Group, Security Curve, Nemertes and pretty much every other analyst firm on the planet. Gartner's ability to exercise their right to remain silent regarding OWASP is interesting but also potentially damaging to their clients.
I can say that both Ounce Labs and Fortify Software also participate in the open source community. It would have been great if they had acknowledged that many of the open source projects that you use in your production infrastructure are using these tools. When you pay attention to open source participation, the vendors start to separate even more.
Anyway, I do hope that Burton Group and Forrester will produce their own documents covering the static analysis space. I know that Chenxi and Blakley respectively will do a lot better job than our friends at Gartner...

| | View blog reactions
Gartner analyst's Joseph Feiman and Neil MacDonald have created the Magic Quadrant for Static Application Security Testing for the fine price of $1,995. Of course they focused on productecture and provided interesting insights into particular vendors such as Ounce Labs, Fortify Software, Coverity, etc but not in a way that is actionable.
For example, they mentioned that Fortify software has a heavy sales model that has annoyed customers but didn't say why this existed. Is it because of the way that products are licensed where folks need to have ongoing interaction with sales folks over the long haul or is it because they have too many sales people that don't have nothing better to do or is it because at some level enterprisey types like the attention and being annoyed is actually a good thing.
Some of my enterprise architect peers love the vendor sales guys. After all, they have an expense account and can take you to fancy restaurants. There is a secret relationship between sales people and enterprise architects that is rarely discussed in public. Some sales guys will allow the enterprise architect to outsource the sales pitch, the dog and pony show the enterprise architect themselves should be doing. So, if you work for one of those shops where you are an enterprise architect but otherwise are clueless, then the commentary of Gartner may not be a negative.
Is security based on superficial things you can count such as number of languages or could it be based on the ability for information to be distilled to non-developer demographics. It is important to acknowledge that static analysis is very useful for helping developers write more secure code but it has a side effect in that it can be used for management purposes as well. Consider a scenario where I may have two Indian outsourcing firms where your otherwise non-technical CIO may want to know whether Cognizant writes more secure code than say Infosys or Wipro. The reporting capabilities may be more important in some shops than its actual ability to help developers.
I find it fascinating that Gartner was notoriously silent on mentioning ways to evaluate static analysis tools. Most folks know that the OWASP WebGoat project serves as a test harness for many of these tools. I have always wondered whether it has anything to do with the fact that other analyst firms have beat Gartner in terms of participation in OWASP? For example, Chenxi Wang of Forrester has participated in user groups and conferences and the same thing can be said of the 451 Group, Security Curve, Nemertes and pretty much every other analyst firm on the planet. Gartner's ability to exercise their right to remain silent regarding OWASP is interesting but also potentially damaging to their clients.
I can say that both Ounce Labs and Fortify Software also participate in the open source community. It would have been great if they had acknowledged that many of the open source projects that you use in your production infrastructure are using these tools. When you pay attention to open source participation, the vendors start to separate even more.
Anyway, I do hope that Burton Group and Forrester will produce their own documents covering the static analysis space. I know that Chenxi and Blakley respectively will do a lot better job than our friends at Gartner...

Enterprise Architecture and Proofs of Concept
Ashraf Motiwala discusses how enterprises conduct vendor POCs yet doesn't talk about practices that vendors should be encouraging.
How many POCs are really glorified ceremonial Hello World's? Enterprises sometimes come up with use cases that are just too simple and don't provide any product differentiation. In the world of identity, taking a feed from HR and provisioning an account in Active Directory is Hello World. So, what are some quick to execute use cases that also happen to be differentiators?
I wonder if Ash believes there is merit in doing SPML interoperability testing? Of course, I would love if Mark Diodati and Gerry Gebel of Burton Group would consider for upcoming Catalyst conference, but if they don't then us clients can do it ourselves. So, can Oracle OIM invoke a SPML web service built using Project Keychain? Can Courion provision a user into a Documentum application using SPML?
I have always wondered whether security products are written securely? If I wanted to steal lots of passwords, should I attack various enterprise applications or would the reward be a lot higher if I attacked identity management platforms since many of them store usernames and passwords either in cleartext or using a reversible algorithm. Does anyone know how Sun, Oracle, Novell and other identity management platforms line up in this regard?
Wouldn't it be funny to know that it is possible to perform a cross-site scripting (XSS) attack against these products? Many of the products and their product managers aren't aware of the OWASP Top Ten and therefore will be ripe for exploitation...

| | View blog reactionsHow many POCs are really glorified ceremonial Hello World's? Enterprises sometimes come up with use cases that are just too simple and don't provide any product differentiation. In the world of identity, taking a feed from HR and provisioning an account in Active Directory is Hello World. So, what are some quick to execute use cases that also happen to be differentiators?
I wonder if Ash believes there is merit in doing SPML interoperability testing? Of course, I would love if Mark Diodati and Gerry Gebel of Burton Group would consider for upcoming Catalyst conference, but if they don't then us clients can do it ourselves. So, can Oracle OIM invoke a SPML web service built using Project Keychain? Can Courion provision a user into a Documentum application using SPML?
I have always wondered whether security products are written securely? If I wanted to steal lots of passwords, should I attack various enterprise applications or would the reward be a lot higher if I attacked identity management platforms since many of them store usernames and passwords either in cleartext or using a reversible algorithm. Does anyone know how Sun, Oracle, Novell and other identity management platforms line up in this regard?
Wouldn't it be funny to know that it is possible to perform a cross-site scripting (XSS) attack against these products? Many of the products and their product managers aren't aware of the OWASP Top Ten and therefore will be ripe for exploitation...

Friday, February 13, 2009
Unix Timestamp
Come join us to watch the countdown (actually up) to the UNIX Epoch time being 1234567890 live on the internet!
It starts now and ends on Saturday at 12:35am...
| | View blog reactionsIt starts now and ends on Saturday at 12:35am...

How come India programmers like to waste their clients time?
A surprisingly large fraction of employees of Indian outsourcing firms, even those with masters' degrees and PhDs in computer science, fail during interviews when asked to carry out basic programming tasks...

I find it fascinating that there are lots of so-called programmers who would apply for a job without being able to write the simplest of programs. Programming is a very error-prone business, especially with "typed-statement" systems. Most of them are very intolerant of errors (even simple typos). You must really have a good conceptual model of how each individual statement and its sub-components effects the result in conjunction with each other statement.
You have to know how to check for proper operation (testing) and how to find out what to fix if it isn't (debugging). Unless you are totally immersed in that particular programming system, understanding the varieties and subtleties of its statements and functions.
Being a programmer isn't for everyone. Maybe folks in India need to practice the Peter Principle more often and move these folks into management. I wonder if you charted a Bell curve for Indian managers who only have one month's worth of experience to those who have had five years, what would be the difference in effectiveness?
Maybe the problem is in how American's like to dumb down problems so that any idiot can understand it. Maybe, we are the reason so many idiots overseas exist? Seriously, compare programming to other professions and you will see a trend emerge. For example, lawyers and tax accountants routinely work with such complexity in their contracts and planning. Doctors work with an untold number of variables. Someone planning a big party has to work out the food, matching paper goods, favors, invitation list, entertainment, etc. The key theme between all of these roles is immersion which is somewhat different than just knowledge transfer or other long arduous but otherwise ineffective methods of exchange.

| | View blog reactions
I find it fascinating that there are lots of so-called programmers who would apply for a job without being able to write the simplest of programs. Programming is a very error-prone business, especially with "typed-statement" systems. Most of them are very intolerant of errors (even simple typos). You must really have a good conceptual model of how each individual statement and its sub-components effects the result in conjunction with each other statement.
You have to know how to check for proper operation (testing) and how to find out what to fix if it isn't (debugging). Unless you are totally immersed in that particular programming system, understanding the varieties and subtleties of its statements and functions.
Being a programmer isn't for everyone. Maybe folks in India need to practice the Peter Principle more often and move these folks into management. I wonder if you charted a Bell curve for Indian managers who only have one month's worth of experience to those who have had five years, what would be the difference in effectiveness?
Maybe the problem is in how American's like to dumb down problems so that any idiot can understand it. Maybe, we are the reason so many idiots overseas exist? Seriously, compare programming to other professions and you will see a trend emerge. For example, lawyers and tax accountants routinely work with such complexity in their contracts and planning. Doctors work with an untold number of variables. Someone planning a big party has to work out the food, matching paper goods, favors, invitation list, entertainment, etc. The key theme between all of these roles is immersion which is somewhat different than just knowledge transfer or other long arduous but otherwise ineffective methods of exchange.

Thursday, February 12, 2009
Random Thoughts for 2009-02-12


Wednesday, February 11, 2009
Enterprise Architecture: What is a worst practice in your organization?
When I talk to my peers who work for other large enterprises, they believe that the root cause of bad IT is the lack of critical thinking and application of disciplined problem solving...

Perception management is getting in the way of disciplined thinking where management proclivity of "just get it done", "throw it over the wall", "we are enterprenural", "fast paced" and so on. In actuality, fast paced should actually be pronounced "half-vast" as in don't start vast projects with half-vast ideas. The problem doesn't lie at the bottom of the food chain; especially in IT, it is a critical incompetency in management starting from enterprise architects to the board.
Outsourcing to India is one of the biggest worst practices ever invented. If a person cannot have a face-to-face conversation, when there is no vested interest in someone in the know helping them out, then the only thing they can leverage is comprehensive documentation. Let's face it:
1. Regardless if you are talking about outsourcing or even regulatory compliance, existing controls have little if any documentation.
2. Processes are almost always intensively manual for no good reason. Things are always more difficult than they need to be.
Have you ever thought about the amount of money that goes unmanaged in the security space? Gunnar Peterson, Gary McGraw, Jeremiah Grossman and others always talk about how much money is wasted on network security and question when software security will get its day in court. I believe the conversation needs to start at making auditing processes at all layers more sane.
Consider what happens when the auditors show up. Out come the spreadsheets. What is a spreadsheet anyway? It is a caveman's database. These tabular views of a situation grow like a cancer requiring rolls of scotch tape in feeble attempts to patch ideas together and present them in a half-vast manner. I don't need to devolve into the intense time and effort to populate, maintain and verify these time killer spreadsheets.
The other side of the coin are the plethora of GRC tools, EA tools (Troux, Alfabet, Metamatrix, etc) where management will almost never take the time to perform a realistic ROI evaluation. These tools elicit emotion-based perception of what the company really needs filled with conjecture, hearsay and superstition.
How come we only have two choices, to either be boneheaded and leverage spreadsheets beyond common sense or to get all enterprisey and piss millions down the toilet on tools we truly don't understand or don't have the long-term discipline to capitalize upon.
This reminds me of the bitch-slap moments whenever someone utters the magic phrase: developing software is not our core business. I wonder if these types will acknowledge that purchasing shelfware isn't their core business either!
Why can't we consider lesser more simple solutions? Instead of wasting time researching and benchmarking who is in the Gartner Magic Quadrant and what our peers in the industry are using because senior management wants to know, only to discover you can't afford it, couldn't we punch ourselves in the face and acknowledge that this may be a clue right there Einstein.
So, is aligning with the business really an IT problem or one of management competency...

| | View blog reactions
Perception management is getting in the way of disciplined thinking where management proclivity of "just get it done", "throw it over the wall", "we are enterprenural", "fast paced" and so on. In actuality, fast paced should actually be pronounced "half-vast" as in don't start vast projects with half-vast ideas. The problem doesn't lie at the bottom of the food chain; especially in IT, it is a critical incompetency in management starting from enterprise architects to the board.
Outsourcing to India is one of the biggest worst practices ever invented. If a person cannot have a face-to-face conversation, when there is no vested interest in someone in the know helping them out, then the only thing they can leverage is comprehensive documentation. Let's face it:
1. Regardless if you are talking about outsourcing or even regulatory compliance, existing controls have little if any documentation.
2. Processes are almost always intensively manual for no good reason. Things are always more difficult than they need to be.
Have you ever thought about the amount of money that goes unmanaged in the security space? Gunnar Peterson, Gary McGraw, Jeremiah Grossman and others always talk about how much money is wasted on network security and question when software security will get its day in court. I believe the conversation needs to start at making auditing processes at all layers more sane.
Consider what happens when the auditors show up. Out come the spreadsheets. What is a spreadsheet anyway? It is a caveman's database. These tabular views of a situation grow like a cancer requiring rolls of scotch tape in feeble attempts to patch ideas together and present them in a half-vast manner. I don't need to devolve into the intense time and effort to populate, maintain and verify these time killer spreadsheets.
The other side of the coin are the plethora of GRC tools, EA tools (Troux, Alfabet, Metamatrix, etc) where management will almost never take the time to perform a realistic ROI evaluation. These tools elicit emotion-based perception of what the company really needs filled with conjecture, hearsay and superstition.
How come we only have two choices, to either be boneheaded and leverage spreadsheets beyond common sense or to get all enterprisey and piss millions down the toilet on tools we truly don't understand or don't have the long-term discipline to capitalize upon.
This reminds me of the bitch-slap moments whenever someone utters the magic phrase: developing software is not our core business. I wonder if these types will acknowledge that purchasing shelfware isn't their core business either!
Why can't we consider lesser more simple solutions? Instead of wasting time researching and benchmarking who is in the Gartner Magic Quadrant and what our peers in the industry are using because senior management wants to know, only to discover you can't afford it, couldn't we punch ourselves in the face and acknowledge that this may be a clue right there Einstein.
So, is aligning with the business really an IT problem or one of management competency...

Tuesday, February 10, 2009
Random Thoughts for 2009-02-10


Monday, February 09, 2009
Should the Application Security community make fun of network engineers who think they are doing security?
Firewalls aren't security, it is network hygiene. CISSP who focus on knowing trivia such as how much lighting is required to illuminate a methadone clinic isn't security. So, instead of throwing daggers at impostor security professionals, I figured I would instead share the URL to our next OWASP meeting which will be available via webinar...
https://www2.gotomeeting.com/register/566470294

| | View blog reactions
Enterprise Architecture: It's 2009 and the business still doesn't understand IT...
Sometimes, I believe that IT is more aligned (in terms of delivery capability, innovation and speed to market) than it is given credit for. The real lack of alignment may be the disconnect between IT and business in that the financial aspect of a solution isn't always completely understood...

Financial aspects of solutions can be very complex as a design may be seem to be the most robust and cost-effective solution in a "snapshot of time" leveraging basic reviews of infrastructure, recurring maintenance and strategic architecture alignment. The financial and vendor relationship management view may not be the top pick of practitioners of enterprise architecture.
We would like to believe that suboptimal decisions to compromise architecture will have financial rewards. The challenge is to see how decisions are made through eyes other than your own. Sure, us IT types believe that business people speak like idiots. The same thing can be said about IT. The complexity of the business and finance roles until one fully engages in their process will be misleading as they are thoughtful once you peel back the layers.
Rather than always bashing process, there is merit in doing research, reaching out to leaders who don't understand enterprise architecture and having the ability to ask dumb questions. One way to tell if you have both a quality process and competent leadership is to have the opportunity to inquire and a channel of communication to improve (aka a process to improve the process)...

| | View blog reactions
Financial aspects of solutions can be very complex as a design may be seem to be the most robust and cost-effective solution in a "snapshot of time" leveraging basic reviews of infrastructure, recurring maintenance and strategic architecture alignment. The financial and vendor relationship management view may not be the top pick of practitioners of enterprise architecture.
We would like to believe that suboptimal decisions to compromise architecture will have financial rewards. The challenge is to see how decisions are made through eyes other than your own. Sure, us IT types believe that business people speak like idiots. The same thing can be said about IT. The complexity of the business and finance roles until one fully engages in their process will be misleading as they are thoughtful once you peel back the layers.
Rather than always bashing process, there is merit in doing research, reaching out to leaders who don't understand enterprise architecture and having the ability to ask dumb questions. One way to tell if you have both a quality process and competent leadership is to have the opportunity to inquire and a channel of communication to improve (aka a process to improve the process)...

Innovation in LDAP
Finally, there is some innovation in LDAP that is worth talking about...

I wonder if Ludovic Poitou believes that LDAP servers should support the XACML protocol or should they continue to only support LDAP-specific ways of providing ACIs?
Bavo De Ridder does mention that so-called referential integrity is not integrity which I agree with. Operations done in a post-operation plug-in can cause semantic integrity challenges. In all reality, referential integrity needs to be combined with transactional support as you need to prevent bad reads. Ever heard of ACID?
One recent innovation comes from Unbound ID which acknowledges that LDAP sucks not from a server perspective but because the right APIs for applications don't exist. Simply put, JNDI is fugly. You would think that Sun out of all companies would be working to come up with something for Java a lot better.
The features that seem beneficial include connection pooling. Isn't it kinda dumb that we are still custom coding connection pools in the world of J2EE application servers? How come Oracle/BEA, Glassfish haven't made this go away. It also seems like they thought a lot about security. Of course, this begs the question of whether LDAP servers should support SAML as an authentication scheme.
I am curious how others think basic operations such as sorting should work in the world of LDAP?

| | View blog reactions
I wonder if Ludovic Poitou believes that LDAP servers should support the XACML protocol or should they continue to only support LDAP-specific ways of providing ACIs?
Bavo De Ridder does mention that so-called referential integrity is not integrity which I agree with. Operations done in a post-operation plug-in can cause semantic integrity challenges. In all reality, referential integrity needs to be combined with transactional support as you need to prevent bad reads. Ever heard of ACID?
One recent innovation comes from Unbound ID which acknowledges that LDAP sucks not from a server perspective but because the right APIs for applications don't exist. Simply put, JNDI is fugly. You would think that Sun out of all companies would be working to come up with something for Java a lot better.
The features that seem beneficial include connection pooling. Isn't it kinda dumb that we are still custom coding connection pools in the world of J2EE application servers? How come Oracle/BEA, Glassfish haven't made this go away. It also seems like they thought a lot about security. Of course, this begs the question of whether LDAP servers should support SAML as an authentication scheme.
I am curious how others think basic operations such as sorting should work in the world of LDAP?

Sunday, February 08, 2009
Enterprise Architecture: What does the Wall Street Meltdown have to do with Indian Outsourcing
In an economic downturn, IT's value to the business can only improve, NOT...

In a market where demand outstrips supply and there are no cost penalties when buying inefficient products, even the most incompetent of management teams could tread water and take in the money. But the moment there are real cost penalties, consumers react by seeking more efficient products. When applying this analogy to IT, the business will either skip Indian outsourcing or create a shadow IT organization that is more efficient.
Regardless of whether we talk about business or IT, this is the free market in operation. It also has the effect of revealing which management teams are asleep and which have some resilience to respond to the economic conditions. Everyone is to blame.
Whether you are a bank, an auto manufacturer or just attempting to deliver IT to the business, executives will accelerate giving the gullible more of what they seem to want and there is no management will to challenge the market's perception. Indeed, to do the right thing such as unwinding credit overload, improving fleet fuel consumption for autos or simply not allowing Indian outsourcing firms to use process as a substitue for competence will require incurring more costs in the short term. This would reduce the dividends to shareholders during the development phase. This would displease everyone. Products would retail at higher prices to recover development costs, profits would stall and the amount of tax payable to the state would drop as the companies write off their development costs. At a time when the government was cutting taxes, this loss of revenue would have been sorely missed. It was, if you care to think of it in this way, a conspiracy of ineptitude and mediocrity in every and all senses of both words...

| | View blog reactions
In a market where demand outstrips supply and there are no cost penalties when buying inefficient products, even the most incompetent of management teams could tread water and take in the money. But the moment there are real cost penalties, consumers react by seeking more efficient products. When applying this analogy to IT, the business will either skip Indian outsourcing or create a shadow IT organization that is more efficient.
Regardless of whether we talk about business or IT, this is the free market in operation. It also has the effect of revealing which management teams are asleep and which have some resilience to respond to the economic conditions. Everyone is to blame.
Whether you are a bank, an auto manufacturer or just attempting to deliver IT to the business, executives will accelerate giving the gullible more of what they seem to want and there is no management will to challenge the market's perception. Indeed, to do the right thing such as unwinding credit overload, improving fleet fuel consumption for autos or simply not allowing Indian outsourcing firms to use process as a substitue for competence will require incurring more costs in the short term. This would reduce the dividends to shareholders during the development phase. This would displease everyone. Products would retail at higher prices to recover development costs, profits would stall and the amount of tax payable to the state would drop as the companies write off their development costs. At a time when the government was cutting taxes, this loss of revenue would have been sorely missed. It was, if you care to think of it in this way, a conspiracy of ineptitude and mediocrity in every and all senses of both words...

Saturday, February 07, 2009
How come the world of Identity doesn't collaborate with the world of Security?
Ever notice how the identity community focuses on the features of security products but never spends any time noodling whether their security products are written securely?
Instead of throwing daggers at the ECM community (Documentum, Stellent, etc), the OpenID community, supports of the Liberty Alliance or even the folks who still haven't figured out that Smalltalk is a dead language, I have decided to take action by making our next meeting of OWASP available via webinar.
We will have Mary Ruddy of Project Higgins and Ramesh Nagappan of Sun as our presenters. Our next meeting is on Tuesday, February 10th at 5pm Eastern in Hartford and is 100% free to attend. For those who can't attend in person, you are welcome to subscribe to our mailing list to receive webinar information...

| | View blog reactionsInstead of throwing daggers at the ECM community (Documentum, Stellent, etc), the OpenID community, supports of the Liberty Alliance or even the folks who still haven't figured out that Smalltalk is a dead language, I have decided to take action by making our next meeting of OWASP available via webinar.
We will have Mary Ruddy of Project Higgins and Ramesh Nagappan of Sun as our presenters. Our next meeting is on Tuesday, February 10th at 5pm Eastern in Hartford and is 100% free to attend. For those who can't attend in person, you are welcome to subscribe to our mailing list to receive webinar information...

Federated Provisioning
Ian Glazer and Nishant Kaushik discuss federated provisioning and provide some high-level scenarios that are somewhat incomplete...

Nishant's example assumes that just-in-time provisioning is about an SP accepting a SAML-based authentication and creating an SPML message. I would argue that there may be multiple business scenarios where you may need something more richer than SPML where federated identity products should also know how to invoke BPEL processes.
If we did such a thing in the insurance vertical, an incoming request isn't just about provisioning access to the system. We may need to kick off a business process where we may need to file paperwork with a state insurance department to appoint that agent in the state they reside, we may need to kick off license checks and even schedule CRM-style a followup call with that person to onboard them.
So, an incoming request may provision a user but will they be effectively provisioned? What happens if just passing attributes aren't enough and I need something more rich like XACML? How does this get mapped into SPML in his scenario? For example, if I provision an insurance agent, I might want to know that he can sell commercial insurance in texas, personal insurance in georgia and life insurance in Oklahoma, Kansas and California. I may want to also understand the structure of his organization so that I can show him commissions of his team but not of others within his organization. Note that this is more than just a discussion about roles.
Anyway, if anyone has thoughts at a deeper level, please share as I think the community would benefit from the insight...

| | View blog reactions
Nishant's example assumes that just-in-time provisioning is about an SP accepting a SAML-based authentication and creating an SPML message. I would argue that there may be multiple business scenarios where you may need something more richer than SPML where federated identity products should also know how to invoke BPEL processes.
If we did such a thing in the insurance vertical, an incoming request isn't just about provisioning access to the system. We may need to kick off a business process where we may need to file paperwork with a state insurance department to appoint that agent in the state they reside, we may need to kick off license checks and even schedule CRM-style a followup call with that person to onboard them.
So, an incoming request may provision a user but will they be effectively provisioned? What happens if just passing attributes aren't enough and I need something more rich like XACML? How does this get mapped into SPML in his scenario? For example, if I provision an insurance agent, I might want to know that he can sell commercial insurance in texas, personal insurance in georgia and life insurance in Oklahoma, Kansas and California. I may want to also understand the structure of his organization so that I can show him commissions of his team but not of others within his organization. Note that this is more than just a discussion about roles.
Anyway, if anyone has thoughts at a deeper level, please share as I think the community would benefit from the insight...




